You'll see a screen similar to the one below when you are infected, this will countdown to zero and literally shut down the system completely. The warning will state "This shutdown was initiated by NT AUTHORITY\SYSTEM".The message will state that the system process lsass.exe terminated unexpectedly.
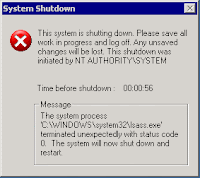
The message may be prefaced by another message:
You can disable this shutdown by following the steps below during the countdown
- Click on Start, Run
- Type, shutdown -a then press enter
How Does Sasser Infect My Computer?
When W32.Sasser.Worm runs, it does the following:
Attempts to create a mutex named Jobaka3l and exits if the attempt fails. This ensures that no more than one instance of the worm can run on the computer any time.
Copies itself as to the %Windir% directory. This is usually the C:\WINDOWS or C:\WINNT directory.
Adds the value:
"avserve.exe"="%Windir%\avserve.exe"
"avserve2.exe"="%Windir%\avserve2.exe"
"skynetave.exe"= "%Windows%\skynetave.exe"
to the following registry key, so that the worm runs on Windows startup.
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
- Uses the AbortSystemShutdown API to hinder attempts to shut down or restart the computer.
- Starts an FTP Server
- on TCP port 5554. This server is used to spread the worm to other hosts.
- Iterates through all the host IP addresses, looking for addresses without any of the following:
- 127.0.0.1
- 10.x.x.x
- 172.16.x.x - 172.31.x.x (inclusive)
- 192.168.x.x
- 169.254.x.x
- Using one of these IP addresses, the worm then generates a random IP address.
52% of the time, the IP address is completely random.
23% of the time, the last three octets are changed to random numbers.
25% of the time, the last two octets are changed to random numbers. - Because the worm can create completely random addresses, any IP range can be infected.
This process is made up of 128 threads, which demands a lot of CPU time. As a result, an infected computer may become so slow and barely usable. - Connects to the randomly generated IP address on TCP port 445 to determine if a remote computer is online.
- If a connection is made to a remote computer, the worm will send shell code to it, which may cause it to open a remote shell on TCP port 9996.
- Uses the shell on the remote computer to connect back to the infected computer's FTP server, running on TCP port 5554, and retrieve a copy of the worm. This copy will have a name consisting of four or five digits, followed by _up.exe. For example, 74354_up.exe.
- The Lsass.exe process will crash after the worm exploits the Windows LSASS vulnerability. Windows will display the alert and shut down the system in 1 minute.
- Creates a file at C:\win.log that contains the IP address of the computer that the worm most recently attempted to infect, as well as the number of infected computers.
How Can I Remove the Sasser worm?
Follow these steps in removing the Sasser worm.- Disconnect your computer from the local area network or Internet
- Terminate the running program
- Open the Windows Task Manager by either pressing CTRL+ALT+DEL, selecting the Processes tab or selecting Task Manager and then the process tab on WinNT/2000/XP machines.
- Locate one of the following programs (depending on variation), click on it and End Task or End Process
avserve.exe
avserve2.exe
skynetave.exe
any process running with the "_up.exe" suffix- Close Task Manager
- Activate the Windows XP Firewall (if running Windows XP) or another firewall to prevent the worm from shutting your system down while downloading the patches. To activate the Windows XP firewall, follow these steps.
- Click on Start, Control Panel
- Double-click on Networking and Internet Connections, then click on Network Connections
- Right-click on the connection you use to access the Internet and choose Properties
- Click on the Advanced Tab and check the box
"Protect my computer and network by limiting or preventing access to this computer from the Internet" - Click OK and close out of the Network and Control Panel
- Download and Install the patches for the LSASS Vulnerability and others
- Microsoft Windows NT® Workstation 4.0 Service Pack 6a
- Microsoft Windows NT Server 4.0 Service Pack 6a
- Microsoft Windows NT Server 4.0 Terminal Server Edition Service Pack 6
- Microsoft Windows 2000 Service Pack 2, Microsoft Windows 2000 Service Pack 3, and Microsoft Windows 2000 Service Pack 4
- Microsoft Windows XP and Microsoft Windows XP Service Pack 1
- Microsoft Windows XP 64-Bit Edition Service Pack 1
- Microsoft Windows XP 64-Bit Edition Version 2003
- Microsoft Windows Server™ 2003
- Microsoft Windows Server 2003 64-Bit Edition
- Remove the Registry entries
- Click on Start, Run, Regedit
- In the left panel go to
- HKEY_LOCAL_MACHINE>Software>Microsoft>Windows>Current Version>Run
- In the right panel, right-click and delete the following entry
"avserve.exe"="%Windir%\avserve.exe"
"avserve2.exe"="%Windir%\avserve2.exe"
"skynetave.exe"= "%Windows%\skynetave.exe"- Close the Registry Editor
- Delete the infected files (for Windows ME and XP remember to turn off System Restore before searching for and deleting these files to remove infected backed up files as well)
- Click Start, point to Find or Search, and then click Files or Folders.
- Make sure that "Look in" is set to (C:\WINDOWS).
- In the "Named" or "Search for..." box, type, or copy and paste, the file names:
avserve.exe
avserve2.exe
skynetave.exe
C:\win2.log
- Click Find Now or Search Now.
- Delete the displayed files.
- Empty the Recycle bin
- Reboot the computer and update your antivirus software, and run a Virus scan with your anti-virus program.
PC Hell
No comments :
Post a Comment
Comment on this Post!!