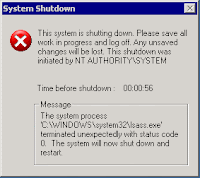
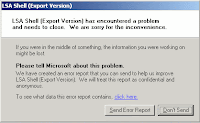
Manual Removal of Bling.exe W32.Spybot.Worm - Removal
Terminating the Malware Program
winnt.exe
bling.exe
Open Windows Task Manager.
On Windows NT, 2000, and XP, press
CTRL+SHIFT+ESC, then click the Processes tab.
- In the list of running programs*, locate the malware file(s).
- Select one of the detected files, then press either the End Task or the End Process button, depending on the version of Windows on your system.
- Do the same for all detected malware files in the list of running processes.
- To check if the malware process has been terminated, close Task Manager, and then open it again.
- Close Task Manager.
Delete the following malicious folders:
X:\Windows\System\kazzabackupfiles\
X:\documents and settings\all users\documents\
[x denotes your windows installed Drive]
Open Registry Editor
Click Start>Run, type REGEDIT, then press Enter.
Delete the following malicious registry entries and\or values:
- Key: System\ControlSet001\Services\Win32 USB2.0 Driver
- Key: System\CurrentControlSet\Enum\Root\LEGACY_WIN32_USB2.0_DRIVER
- Key: System\CurrentControlSet\Services\Win32 USB2.0 Driver
- Key: software\microsoft\windows\currentversion\runOnce Value: Configuration Update
- Key: software\microsoft\windows\currentversion\runOnce Value: nodriver
- Key: software\microsoft\windows\currentversion\runOnce Value: NvCpl28Deamon
- Key: Software\Microsoft\Windows\CurrentVersion\Runonce Value: OEM32 Tools
- Key: software\microsoft\windows\currentversion\runOnce Value: PopUp Stopper
- Key: software\microsoft\windows\currentversion\runOnce Value: TaskManager Load Module
- Key: software\microsoft\windows\currentversion\runOnce Value: UpdateCheck
- Key: Software\Microsoft\Windows\CurrentVersion\RunOnce Value: Win startup
- Key: Software\Microsoft\Windows\CurrentVersion\RunOnce Value: Win32 USB2.0 Driver
- Key: software\microsoft\windows\currentversion\runOnce Value: Winampa Agent
- Key: software\microsoft\windows\currentversion\runOnce Value: Windows Logon
- Key: software\microsoft\windows\currentversion\runOnce Value: Winsock2 driver
- Key: software\microsoft\windows\currentversion\runOnce Value: winsockdriver
These files are also infected, to remove you need to use any antivirus program like Kaspersky, Nod32, Bitdefender, Avg or any other.
|
0bfe88af511af8????1426ed3158de0c.exe
0f0????d1be50b4b04f28cb0c3f6bf0c.exe
0facec44e61f248cd65b1ec3f????3cb.exe
142efb7a7cf????a0d3d7da308ee6e9c.exe
1c8467b3d3b????e770b34683aa834fc.exe
1fcc????04af6f0484dd0a10ea317b2d.exe
287b93f27195b664b7f6d????848dd10.exe
2ce4b9d369b51be7ce????9f6e25e020.exe
2d6a1e49a1d17990c6f3724b????296c.exe
326210a48b8ae????c4dae6d20fe921d.exe
33604b93dd6254892572????12dc41c3.exe
36b184????63cd65a002cc31065e4e45.exe
36b5c5de76cedd4f72c0890????85aac.exe
39863834360409913ccb8670f9????f8.exe
3b0????31ff59868657dfcee37d82642.exe
42c9f9????893d2005a62e151b7c1575.exe
4ae5d594bff????82bd18956bc500a7b.exe
4aeebc5056522dbe5b95????354d2b78.exe
4eb3a4f964b13e09ad7????e0f231c97.exe
51df311f3b5360973275f????576788d.exe
5b50bab4afbd76d180ef5????ce6e37f.exe
709b055a????a05fd4c5fbc20c798c3f.exe
7247be51????e4b71aaa9bf22fd09169.exe
729552ad51eeec0????21e5b84c5474d.exe
76ff839cc1785dddf5????f33ab4f89b.exe
77553a4544b0a47986195????3bfa598.exe
79f8b8????7894d24391f445fb8637d6.exe
7b459c739bdb83f6ce????a5a9e4202b.exe
885d0f9a33208ed13????30888e4e50e.exe
88a034dcfc4a5bca1????28a34c81a78.exe
891????e09f2d9d9aa27a268604255eb.exe
8dba0ffe????eef9d27ec4e3017246d6.exe
9183013a????4f857948d7b299d1c2bc.exe
92a1ad5bb921d59d5537????a2bde798.exe
93f6c8cb294????32bdbae5755530ba8.exe
998ea3f85e937f2cb91c08517????ea9.exe
9b5d25fb343e8c2108a????be03802e9.exe
a410ca36a2b97214e29a????a6a0fe7a.exe
a93776ce2d3ad361d8aea2????0aab7f.exe
aa1395349d19c3c00????e3fc0ee060b.exe
aa88162e????22e9a18df61563974e1e.exe
ab5234ea993????2ffb0a9d6ced65661.exe
acbce1436d2795a3980????d062a6879.exe
b1ba7b54????3b8dc784b0b49d3f8bcb.exe
b6d1f1bf5d????7f5b7e7481a62770cc.exe
b9e4a2411381????e45ba03161984593.exe
bd04dea1effe5c1340b3e549e2????32.exe
d12213fd5f946????a0e5c191c13c7cc.exe
d2c73b589336af6????5cf150c961f01.exe
d4deabaacf7d0b82fb47????697e13c3.exe
d5205d683f8eda61f????f974d1a268b.exe
dcc48b????1e27f67443576a79d96ac3.exe
ddba39e4e6f2????6e4e58879b699965.exe
e2dd82cbabe2????b9543868ea1d7c88.exe
e74c3e1212389c35df82????a06c8a6f.exe
e88450528????4a2ad22d0690d35483c.exe
e9b8c8cfa3e6641c38247????fcd1581.exe
ed4e11e7784d7????4f4810663f7a7bd.exe
efea2a6506391145f83????9eb465c18.exe
f0d2b32723052048c????ce12643ca10.exe
f27fed8c2057bb3c7b3012e3????bcdb.exe
f2b4ed????e600a5485c149ab8944785.exe
f4aa????319191f99c42d94dd4b4881d.exe
f604b64d79????98476c9a5b6ce63851.exe
f76f6b059e1f7????d1ab10278ee9626.exe
fb220e0d3975c10????ba8f1ffd3e1ca.exe
fd3488d1a6b98460c9d655b1c????fb3.exe |
Removing Autostart Entries from the Registry
Removing autostart entries from the registry prevents the malware from executing at startup.
Open Registry Editor.
Click Start > Run. Type regedit Click OK.
Note: If the registry editor fails to open the threat may have modified the registry to prevent access to the registry editor. Download and run this UnHookExec.inf, and then continue with the removal.
Right-click the UnHookExec.inf file and click install. (This is a small file. It does not display any notice or boxes when you run it.)
Click OK.
In the Registry Editor, navigate to the following subkeys:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\
RunOnce
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\
RunServices
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\
RunServices
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\
RunOnce
HKEY_CURRENT_USER\Software\Microsoft\OLE
In the right pane, delete any values that refer to the file names that were detected.
Navigate to the subkeys:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\SharedAccess
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\wscsvc
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\TlntSvr
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\RemoteRegistry
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Messenger
In the right pane, reset the original value, if known:
"Start" = "4"
Navigate to the subkey:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa
In the right pane, reset the original value, if known:
"restrictanonymous" = "1"
Navigate to the subkey:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\lanmanserver\
parameters
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\lanmanworkstation\
parameters
In the right pane, reset the original values, if known:
"AutoShareWks" = "0"
"AutoShareServer" = "0"
Navigate to the subkey:
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate
In the right pane, reset the original value, if known:
"DoNotAllowXPSP2" = "1"
Navigate to the subkey:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\OLE
In the right pane, reset the original value, if known:
"EnableDCOM" = "N"
Navigate to and delete the following subkeys, if present:
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\BoolTern
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Enum\Root\LEGACY_BOOLTERN
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\rdriv
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Enum\Root\LEGACY_RDRIV
Exit the Registry Editor.
Windows XP Service Pack 2
If you are running Windows XP with Service Pack 2 and are using the Windows Firewall, the operating system will alert you when the SharedAccess service is stopped, by displaying an alert balloon saying that your Firewall status is unknown. Perform the following steps to ensure that the Windows Firewall is re-enabled:
Click Start > Control Panel.
Double-click the Security Center.
Ensure that the Firewall security essential is marked ON.
Note: If the Firewall security essential is marked on, your Windows Firewall is on and you do not need to continue with these steps.
If the Firewall security essential is not marked on, click the "Recommendations" button.
Under "Recommendations," click Enable Now. A window appears telling you that the Windows Firewall was successfully turned on.
Click Close, and then click OK.
Close the Security Center.
Recommended Removal Tools:
Kaspersky Antivirus or Internet Security (Shareware)
Spyware Doctor (Shareware)
AVG Antivirus (Freeware)